Hello, my friends! Welcome to my blog. In this post, we will delve into Blockchain, a technology that is pretty famous for its use with digital money. But is that all that it can be done with Blockchain? Let’s find out!
Bitcoin

The year was 2008. The global financial crisis brings down financial companies such as the Lehman Brothers. The crisis has spawned several discussions about economic systems, such as wealth centralization.
In a traditional economic system, we have money centralized in governments, moreover in banks, without real control of the capital’s owners, that is the people, from whom the capital was obtained.
With this in mind, Satoshi Nakamoto – a person, or group of persons, since was never discovered the true identity – launched a paper proposing a peer-to-peer network payment system, where value (wealth) would be transferred by a decentralized, irreversible transaction network. With decentralized, it means there is no universal authority responsible for validating transactions, using a consensus mechanism, where the network itself validates the transactions.
And by irreversible, it means that, once a transaction is written on the network, it can’t be changed anymore. The database system, where the transactions are persisted, it is called Blockchain. A Blockchain is composed of blocks of transactions, linked together as a chain, hence the name. A block, in this context, consists of a data structure, like a row in an accounting book, or a register in a database, for example.
Also, since transactions can’t be tampered with, the Blockchain can be easily accessed, in an open, public way, typically with applications developed as browsers for the network, called Blockchain Explorers.
On a Blockchain, each user is identified by an address. An address consists of a hash id (more on that later), which can send and receive transactions, using a wallet. The currency inside the Blockchain has the same name as the technology, Bitcoin, with the “cents” equivalent being called Satoshis. Bitcoin uses 8 decimal places for value, allowing a much more precise value definition than traditional currencies.
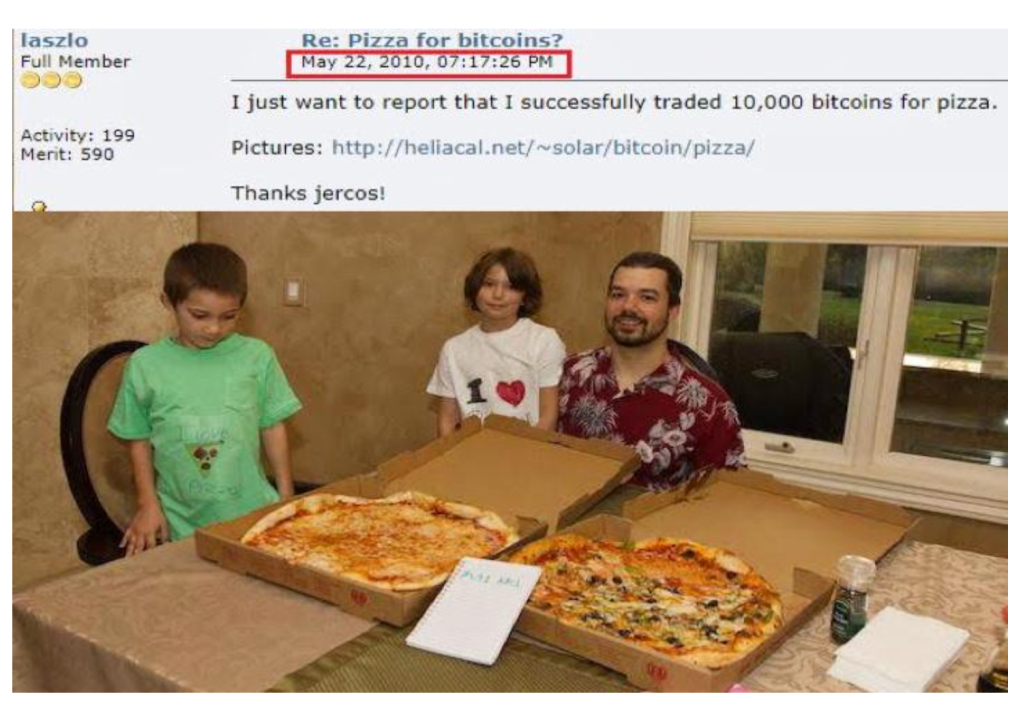
On January 2009, Bitcoin was launched, with the first block in the network being mined by Nakamoto. Several people that were creators of digital currencies before Bitcoin have received coins, like Wei Dai and Nick Szabo. The first commercial transaction using Bitcoin was done in 2010 when two pizzas were bought in the Papa John’s Pizza food chain.
Today, Bitcoin is the oldest and more valuable digital currency in the world, evaluating about 17,413.90 US dollars by today’s value (12-15-2022).
For achieving validation, Bitcoin uses a consensus mechanism called PoW (Proof-of-Work). This mechanism uses very CPU-intensive computations for defining the validator responsible for writing the next block on the chain (we will learn more about this soon). These computations are very hardware-demanding, incurring more processing power (hardware) and consequently, more energy to run that hardware. This incurs Bitcoin receiving heavy criticism about its environmental impact since lots of energy was spent on hardware to improve the chances of receiving transaction fees from the Blockchain.
For some years, Bitcoin reigned alone in the digital currencies ecosystem. However, as we will see next, that was about to change.
Ethereum

Ethereum was conceived in 2013, by russian-canadian programmer Vitalik Buterin, alongside other founders such as Charles Hoskinson. The network was developed in 2014 and went live on July 2015. It is the second most valuable digital coin in the world, second only to Bitcoin.
Ethereum operates a Blockchain network following the same principles as Bitcoin, such as decentralized validation and immutability. However, Ethereum not only implements a digital asset, but also a framework for the implementation and deployment of Smart Contracts. Smart Contracts, as we will learn, consist of a schema for developing dApps (Decentralized Apps), that is, apps that run in the Blockchain. These apps manipulate tokens, allowing users to transfer and receive value in a secure and auditable way.
Recently in Ethereum’s history, a major event changed Ethereum’s technical architecture, called The Merge. This event made the change in the consensus mechanism used by Ethereum from PoW to PoS (Proof-of-Stake). This mechanism, which implements a much more eco-friendly approach, is claimed to have reduced Ethereum energy costs by 99,95%.
Ethereum revolutionized the way digital assets are implemented, allowing a booming of literal thousands of other coins, as we will see next.
AltCoins

Altcoins, as the name implies, is used for referring to basically every coin alternative to Bitcoin. By supplying a tokenizing method, Ethereum opened the door to a digital coins explosion, with literally thousands of coins being offered at exchanges. According to coinmarketcap, there are about 22,088 coins currently in operation.
Is it true that some coins were created from Bitcoin forks, such as Monero, but is undeniable that Ethereum was the major player in this revolution. Famous coins that run on Ethereum are Tether, Cardano, and Solana. Cardano is one of the most valuable of Ethereum’s “children“, created by Charles Hoskinson, one of Ethereum’s co-founders.
Altcoins use different strategies, according to their “philosophies“. We have coins that are called private coins, that implement extra features focused on obfuscating the origin and destinations of Blockchain’s transactions, focusing on keeping the user’s privacies. These coins are particularly in check by governments, as this sadly also facilitates these coins to be used in illegal activities, such as money laundering. Examples of these coins are Monero and PIVX.
Other coins are called stablecoins, which implement different mechanisms with the promise of being “stable investments”. One example is Tether, a coin that promises to keep parity of 1 Tether for 1 US Dollar. A catastrophic event occurred in 2022, where the coin Terra Luna “stablecoin” crashed, losing much of its value. This is an alert for investment in cryptocurrencies, which must be done with caution and care, as it is a highly speculative business.
Blockchain concepts
As we learned before, a Blockchain consists of a block list, where each block has a link (actually, a hash, as we will learn later) for its previous block in the chain. This way, we ensure data can’t be changed once is properly written in a block.
Now, let’s make a tour of the computing concepts behind Blockchain, to get a deeper view of the technology.
Asymmetric cryptography
In computing, cryptography is used for encrypting data, in order to secure information from being read by malicious and/or unauthorized entities.
Asymmetric cryptography is a category of algorithms where we have two keys, a public key, and a private key. In these algorithms, the public key is used for encryption, and the private key is used for decryption. These keys are created at the same time, forming a key pair. Examples of algorithms that use this scheme are RSA, DSA, ECC, and ECDSA (the one used by Bitcoin).
Is not possible to decrypt data using a private key which encryption was not done by the correspondent public key, even if it is a valid private key, according to the algorithm. This way, only by using the correct key pair is it possible to make the encryption.
Another use case for asymmetric cryptography is for digital signatures. On algorithms like ECDSA, the private key is used for signing (generating a hash, based on data passed to the signature), and it can only be considered valid upon a validation method, using the public key. This way, only the correct private key can generate signatures that the correspondent public key can validate.
Now that we understood how asymmetric cryptography works, let’s learn how Blockchain uses it to leverage security for the users to send and receive their coins.
Wallet concepts
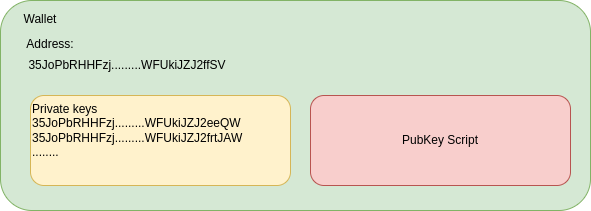
A wallet inside Bitcoin is a user’s identification and storage, allowing him to send and receive coins. A wallet consists of the following components:
- A Blockchain address;
- A private key, for generating signatures;
- A PubKey script, for locking the coins from being spent without authorization.
When we open a Bitcoin client for the first time and ask to create a wallet for us, these components are created. As we learned before, private keys are used for signing transactions, and public keys are used for validating the signatures.
The reader is probably thinking “where is the public key?”. Bitcoin uses a slightly different approach. Instead of using just one private key and one public key for signing all wallet transactions, each transaction has its own private and public keys.
The private key created at the wallet creation is called the master private key. She is used for creating the key pairs used on the wallet transactions. The master private key can be restored by passing a seed, that consists of a string sequence used to recreate the key. These seeds are the famous secret passphrases supplied when the wallet is created.
If the secret passphrase is lost and the wallet is in a locked state, there is no way to recover the coins, resulting in the famous cases of people that lost thousands of dollars on irrecoverable bitcoins.
When the master private key is created for the first time, of course, there is also a public key generated. This public key is used for just one step before being thrown away, and that is to generate the Blockchain address. On Bitcoin’s implementation, the Blockchain address is basically just a compressed version of the public key, prefaced with “00“. The compression is done by using a base58check function.
Lastly, let’s talk about the PubKey script. Wallets implement a locking mechanism in order to secure the coins from being just “left open” for spending. When we want to spend coins from our wallet, the private key is supplied for the PubKey Script, which validates if the coins can be unlocked or not. The script uses a combination of the private key with all public keys from received transactions in the wallet, this way ensuring that only the owner of the wallet’s private key can unlock the coins for the transaction.
So basically, this is a wallet, an address, a group of private keys (the one created with the seed and all the ones used for sending coins), and a PubKey script for securing the coins from being spent from anyone else than the owner. To know the wallet’s balance, the wallet calculates the transactions received that contain unspent coins (we will know more about unspent transactions when learning about UTXO).
Now that we know about how the wallet works, let’s learn about how the blocks in the chain are formed.
Block structure
Block hashes & linkage
So, as we learned previously, Bitcoin’s wallet uses hashes to sign that their transactions are legit. To validate and link the blocks, the same principle is applied.
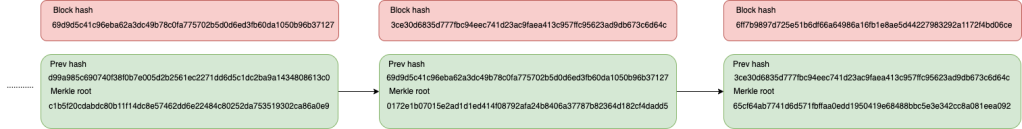
Bitcoin’s blocks are linked using the block’s header. A block header has two hashes, calculated using SHA-256. The first hash, called hashPrevBlock, as the name implies, is the hash of the previous block.
The block hash, which is used as a reference in the field, is calculated by applying a double SHA-256 on the block header data, that is the previous hash – the block hash from the previous block -, the Merkle root – more on that next – and other data, such as the timestamp from when the block was created. If a single bit of this data is changed, the resulting hash will be completely different from the original hash.
The other hash is the hashMerkleRoot. This hash is also a double SHA256, made by all transaction data, including the signature hashes from the transactions processed on this block.
The following diagram illustrates how the blockchain and the hashes work in practice:
So, as we can see, the link is established by hash references, as the next block in the chain has a reference to the previous one. This is what guarantees there is no tampering on the blockchain. Why? Let’s see an example.
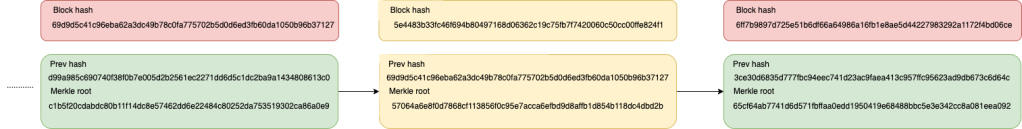
Let’s suppose we want to overwrite one transaction on our middle block from our previous example. This would be the result of this tampering:
As we can see, when we change transaction data, we change the Merkle root, and also, as consequence, we change our block’s hash. And since the next block has a reference to the original block, not the new one, the tampering can’t enter the network, as it is not recognized by the network’s nodes. The process of making a block valid on Bitcoin is called mining, as we will see in the next sections, and involves computations to make it harder to achieve since is a remunerable activity.
And so, since is hard to achieve for just one block, imagine achieving the mining rights not only for the tampered block but also for all blocks upstream, all the way up to the chain’s head. Not to mention, new blocks are created about every 10 minutes, making it also a race to catch up with the head in order to successfully achieve the transaction adulteration.
All this effort to change the data is what makes Blockchain virtually immune to adulteration, making it a secure storage for immutable data, in this case, financial value.
Block transactions
A block on the Blockchain also has a transaction section. This section has a list of transactions, composed of inputs (the coins that will be used for sending in the block), outputs (the coins receivers), and hash signatures, from the addresses that are sending their coins, in order to validate their authenticity.
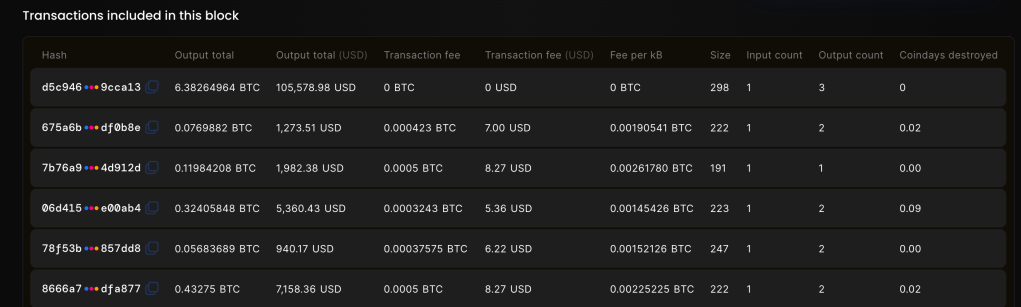
The following image shows an example transaction section of a Bitcoin block:
We can see other information as well, such as the transaction fee, gained by the miner, and the number of inputs and outputs each transaction has. Finally, the coindays destroyed metric is used to measure how many days the coins remained on the input address before being spent. This is used to help track long-term investors and big players in the network’s economy.
Now that we have a general understanding of what a block is, how they are connected, and their structure, let’s understand what happens when we ask to send some coins from our addresses to another on Bitcoin, in order to understand the inner workings of the network in practice.
What happens when you ask to send a Bitcoin
Mining
Bitcoin’s blockchain network is composed of nodes. Nodes are responsible for validating the transactions inside a block, as well as agreeing upon a new block to be added to the chain. The act of generating a new block is called mining, hence the nodes are also called miners.
New blocks are mined every ten minutes. To generate a new block, all a miner has to do is generate a valid block hash, which must be a number below the target. SHA-256 hashes can be transformed into hexadecimal numbers, this way allowing the target’s comparison
The target is a global network parameter that defines the difficulty to generate a new block. This number dynamically fluctuates automatically, as the network increases or decreases in node numbers. This ensures the 10-minute block generation is maintained, and also ensures the increases won’t result in blocks being mined easier. This is important, due to mining results being a paid activity since the miner receives a fee for creating a new block.
Miners validate UTXO transactions, which are a special type of transaction that protects the system from a double spending exploit.
UTXO transactions
In the previous section, we talked about the double spending exploit. This exploit consists of using a delay in transaction validation on a financial system, making an account send the same value twice or more times to a given destination, making the multiple sents to be validated, by making the transactions quicker than the system can validate them.
Blockchain protects the system from this exploit by using UTXO (Unspent Transaction Output) transactions. UTXO transactions are transactions that contain unspent coins, that is, transactions that were received by one address and not sent to another.
The Blockchain network has a monitor, called UTXO Monitor, which is controlled by the nodes to keep track of the unspent transactions. Only transactions in this state can be accepted as inputs in a block. let’s see a real-life example to better understand how this works.
Let’s suppose Ana wants to pay $70 to Alexandre. Ana only has two money bills, each of $50. So, in order to pay Alexandre, Ana gives the two bills to Alexandre, as we can see below:
However, since Ana wants to pay $70, not $100, Alexandre needs to give change to Ana, in this case, $30:
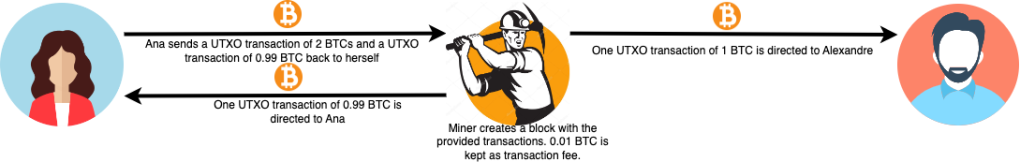
The same thing applies to UTXO transactions in Bitcoin. Suppose Ana wants to send 1 BTC to Alexandre. She has a UTXO transaction of 2 Bitcoins that she can supply as input and is willing to pay 0.01 BTC as the transaction fee. In this case, two UTXO transactions are generated as outputs, one of 1 BTC to Alexandre and one of 0.99 BTC to herself. This ensures that there is no double spending since the wallet’s balance can only be spent by resources that are monitored and agreed upon by the whole network.
The following image illustrates the UTXOs dynamic from the previous example:
Transaction fees are defined by the clients and can be set on the wallet and changed from one transaction to another. Of course, miners can prioritize the transactions that offer the highest fees, so the higher the fee, the better the chance that the transaction will be chosen to be processed on the next block. All pending transactions are maintained on a pool in the network. The miners calculate how much fee they will receive on a transaction by summing it up all inputs and outputs involved in the transaction.
Inside Bitcoin’s architecture, there is a special event that happens every few years called the halving. In this event, a parameter is introduced in the miner’s fees calculation, in order to diminish the amount of the fees (on the next one, which will happen in a few years, it will drop by half the transaction fee values). This measure is made in order to ensure Bitcoin’s value, in order to slow down the coin’s supply. Think like measures done by governments to control inflation on fiat currencies.
So that’s how transactions work. But how the blocks itself are validated in order to enter the Blockchain?
How the block is validated
As we learned before, miners constantly try to generate valid hashes, that must also be lower than the global target setting. When a miner finds a valid hash for mining, it sends a broadcast of his valid block, with the block hash and all data it composes (both header and transactions section).
As miners receive the proposed new block, they validate not only the block hash but also all transactions added to the block. Is during this step that the miners validate if the transaction hashes (signatures) are valid, by using the public key.
This ensures that the coins are really sent by someone who has access to the wallet’s private keys since the public key and hash provided can only be generated by the wallet’s private key.
We could be thinking “what happens if more than one miner generates a valid block at the same time?”. In order to fix this problem, when a miner broadcasts a block, the miners on the network start signaling that accept the block, as they validate it.
If multiple miners broadcast valid blocks at the same time, we enter a race condition, where different blocks are validated by different miners at different paces. The first block that is validated by 50% of the nodes in the network is considered the winner of the “race”, so only he is accepted, and the miner receives his fee.
All the other blocks that are disputed to be valid are discarded, where they enter a state called orphan since the block created a chain that is not accepted by the network.
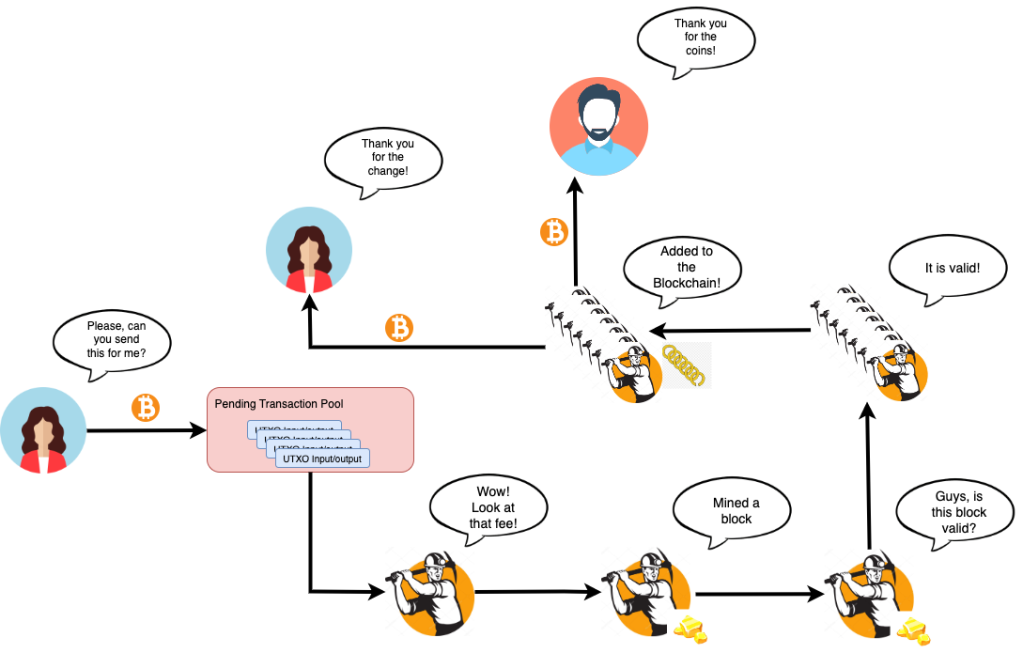
So, in a nutshell, this is what happens when we send Bitcoin to someone on the Blockchain:
- we send from our wallet UTXO transactions as input funds, alongside the amount to be sent, the destination, and finally, the proposed output UTXO transaction that is the “change” to give back to us, and sign the transaction;
- The transaction goes to a pool, where miners scan for transactions to process;
- A miner generates a valid block with our transaction, and broadcasts it to the network for validation;
- If sufficient miners validate the block, he is accepted and added to the chain;
- The funds are delivered to the destination. If there are more coins on the input than the amount sent plus the transaction fee, the change is delivered back to us as the output UTXO transaction, minus the miner fee, which is kept for the miner.
This comic stripe explains, in a humorous way, the process of a Bitcoin transaction:
As we saw before, this PoW consensus model used by Bitcoin is very hardware demanding, making it one the most detractive points of the technology. However, as new coins are born, new consensus models are been developed.
Consensus models
As new coins and Blockchain systems were born, so it emerged new consensus models. Let’s delve a little into some of the other ones that are currently in use.
The second most known consensus model is called PoS, or Proof of Stake. In this model, instead of generating hashes, the validators (on PoS blockchains, the nodes are called validators, as there is no mining in this case) are randomly chosen by the network to create the new block, so no hardware-intensive competition is done.
This model has other types of criticism, however, as each Blockchain tends to add randomizing parameters that are not standard to all networks, and not always is clear how it works. Another common criticism is that it incentives the eternal “division of class” inside the network, as the most common influence parameter to be selected to create a block is the number of coins inside the validator (hence the term stake, referring to the coins deposited inside the validator).
Another consensus model is PoH (Proof of History), where the validators must answer problems from the history of the Blockchain, like in a “quiz show” (a transaction is randomly selected and is questioned if it happened before or after another transaction. Whoever answer correctly first, wins the right to create the block). As this kind of problem is more memory-intensive than CPU-intensive, the energy cost that plagues the PoW model is not as problematic in this case.
As the technology evolves more and more, new models will appear, improving the robustness and solving the problems of today’s implementations.
Now that we take a grasp of Blockchain technology architecture, let’s move on to learn more about Ethereum, and its proposal to revolutionize secure applications. It is important to notice that, aside from differences here and there – Ethereum for example uses a different hash algorithm than Bitcoin – most of the concepts and design on all other crypto coins follow closely to what Bitcoin pioneered, making an excellent central point to learn the technology.
Ethereum & blockchain revolution
Smart Contracts (dApps)

Up until now, we have learned about Bitcoin primarily. Bitcoin is an architecture designed for a single purpose, which is for creating a cryptocurrency.
Ethereum, on the other hand, has a more diverse proposal. Not only is it a cryptocurrency, but also a platform for developing applications that run on top of the Blockchain. These apps are called dApps, or Decentralized Apps.
The term refers to the Blockchain architecture, which has decentralized processing, as we saw during our study.
These applications are developed by deploying a Smart Contract. A Smart Contract is a definition, much like an interface, that defines the functions that will be implemented by the application. The contract, alongside his implementation, is deployed on the Blockchain, much like an application package. dApps are developed using the Solidity language.
Considerations must be taken when developing a dApp. dApps doesn’t have access to external resources, that is, resources outside the network (also referred to as off-chain resources). All persistence is done at the Blockchain, which is persisted as tokens. The persistence on dApps is a major point to pay attention to. As Blockchain data can’t be changed after is validated, one mistake done at the persistence layer can only be solved without the implication of correcting historical data, as there is no possible way of changing already persisted data.
Another hyped term in this field is Web3. On Web3, we have dApps serving as the back-end to web applications. This expands tremendously the applications of Blockchain, by becoming a lot more accessible to users around the world.
dApps are a subject that deserves an article of their own. Stay tuned for an article specially focused on dApps in the future!
Tokens
Last section we talked about tokens. Tokens on Ethereum are the data that can be generated and/or distributed across addresses on the network. So, with this context in mind, we can say the coins themselves – called ether in Ethereum – are tokens, since, in the end, coins on the network are data inside the network, being transferred from address to address.
Ethereum introduces a new standard for tokens, called ERC-20. This standard defines a pattern for Fungible tokens. Fungible tokens are tokens that represent value, such as Ether – but they are not the same, as Ether is the standard token used for payment in the network, while fungible tokens are a representation of value built on top of the network -, that can be interchanged between addresses.
Many AltCoins that circulate today are, from the inside, Fungible Tokens inside Ethereum. Examples are:
- Tether USD;
- USD Coin;
- Shiba Inu;
- BNB;
- etc.
NFTs

Probably all of us have heard of NFTs. Traded at very high prices, we see people across the world paying for buying things like a monkey gif set, for example. But what are NFTs, after all?
NFT stands for Non-Fungible Token. That’s right, NFTs are nothing more than tokens inside Ethereum’s network. They are implemented by the ERC-721 standard. What makes them different from the ERC-20 ones is that they are the antithesis of the ERC-20 tokens: they are unique.
By unique, it means that they have properties that make them 100% different from any other token that can be created on Ethereum’s network. The standard establishes that metadata can be persisted at the Token’s creation and that no other token can be created with that same metadata.
These characteristics are what makes the NFTs evaluated so high: the exclusive ownership of something that no one else in the entire world can have.
Is not in the scope of this article to discuss the morality or meaning of the NFT market, so this subject won’t be touched. However, one thing to keep in mind is the applications that NFTs open for business, as the uniqueness of NFTs aligned with the secure and immutable nature of the Blockchain, allows us to build solutions where these types of tokens can be used to persist information, like documents, for example. One example is the mortgage company LoanSnap, which adopted NFTs to secure its mortgage contracts.
Private Blockchains
Up until now, we just talked about Ethereum’s public network. But that is not the only possible way to run and use the Ethereum network.
Ethereum is open-source software. That means that anyone can take some computers and run their own network – given time to study the complexities of running a network, of course.
As it is not the goal of a company to know the entrails of Blockchain’s network and some companies may have regulations that forbid the data to be available to the public, as much as Ethereum’s network is secure as it is, a private network – and consequently, Blockchain – is made necessary.
Some companies, like Kaleido, have cloud Blockchains available. Using cloud computing vendors such as AWS, allows the creation of private Blockchains, with NFTs and ERC-20 tokens as we see fit.
Consortiums
Consortiums are industry-wide groups, intended to establish standards for the adoption and integration of Blockchain applications across companies in the same business field. This reminds us of another good application for Blockchain: as a secure and auditable global network, it is possible to use Blockchain as an integration layer across companies.
There are several consortia from different business groups across the globe, such as BiTA (Logistics) and Hashed Health (HealthCare).
Conclusion
Phew, that was a lot to cover! Blockchain is a technology in his youth, full of concepts and potential. This article aimed to make a general view of the technology, as the basis for future specific studies in this field.
But this is not the end of our journey. In the future, we will revisit this world, this time focused on the dApps ecosystem and development. Thank you for following me one more time, until next time!
Acknowledgments
Thank you for following me and supporting this blog, by visiting and sharing the knowledge, it means very much to me! Also thanks to Loggi, which supported me in my Blockchain courses, it helped a lot in my studies, thank you!
And as we talked about blockchain and cryptocurrencies, If you kindly wanna support me on my adventures in producing content, feel free to donate a crypto coin to me. If you prefer to donate Neblios (NEBL), please donate to:
Ni239Wqwvp12eHNnbXGbo6BwFbBhwF13L5
And if you prefer to donate Ethereum (ETH), please donate to:
0x2D9A0781872aCe96365d2b20b3ce905E0473981D
Please keep in mind that this is entirely optional and it won’t stop me from producing content whatsoever, it is just a possible way to express recognition of my effort, and I will be very grateful on my part!
Thank you for following me on another post, until next time!